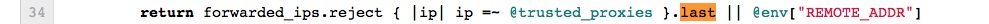This affects the security of internal webservers with rails-web-apps (Intranet-Servers, ...)
affected: request.remote_ip
rails/actionpack/lib/action_dispatch/middleware/remote_ip.rb method: to_s
rails/actionpack/lib/action_dispatch/http/request.rb
possible attacks (on intranet webapps):
x ip spoofing
x logfile-injection
-- ipspoofing
-- date back attack (hide)
-- binary injection to mess with analysing-tools
if request.remote_ip is used in an insecure manner
- Persistent XSS
- SQL-Injection (if request.remote_ip is used in an insecure sql-query)
...
(i would have trusted request.remote_ip)
quick-fix:
check if "request.remote_ip" is really an ip-address before you use it
proof-of-concept:
1.
https://gist.github.com/868268
2.
Screencast shows you a POC with tamperdata.
Persistent XSS with Devise, IP-Spoofing, ...
you can leave anonymous comments
http://www.jimmybandit.com