This affects the security of internal webservers with rails-web-apps (Intranet-Servers, ...)
affected: request.remote_ip
rails/actionpack/lib/action_dispatch/middleware/remote_ip.rb method: to_s
rails/actionpack/lib/action_dispatch/http/request.rb
possible attacks (on intranet webapps):
x ip spoofing
x logfile-injection
-- ipspoofing
-- date back attack (hide)
-- binary injection to mess with analysing-tools
if request.remote_ip is used in an insecure manner
- Persistent XSS
- SQL-Injection (if request.remote_ip is used in an insecure sql-query)
...
(i would have trusted request.remote_ip)
quick-fix:
check if "request.remote_ip" is really an ip-address before you use it
proof-of-concept:
1.
https://gist.github.com/868268
2.
Screencast shows you a POC with tamperdata.
Persistent XSS with Devise, IP-Spoofing, ...
you can leave anonymous comments
http://www.jimmybandit.com
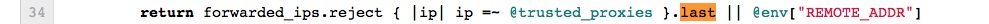

ruby on rails web development
AntwortenLöschenRUBY ON RAILS CUSTOM WEB APPLICATION SERVICES
AntwortenLöschenWebimiz ile kaliteli casinolar oynabilirsiniz. Venüsbet Venüsbet Grandbetting Grandbetting Hiltonbet Betnano Marsbahis Meritking Asyabahis
AntwortenLöschenخرید نهال بادام
AntwortenLöschenEn Son Çıkan Perde Modelleri
AntwortenLöschenSms onay
mobil ödeme bozdurma
nft nasıl alınır
Ankara evden eve nakliyat
trafik sigortası
dedektör
web sitesi kurma
Aşk romanları
You can do very creative work in a particular field. Exceptional concept That was incredible share. Taxi Driver Jacket
AntwortenLöschenCongratulations on your article, it was very helpful and successful. 8036f428576fa8ce866915307203d0c1
AntwortenLöschensms onay
website kurma
website kurma
Thank you for your explanation, very good content. ec2879f4873305df839aad529de18dfa
AntwortenLöschenaltın dedektörü
Good content. You write beautiful things.
AntwortenLöschenkorsan taksi
sportsbet
taksi
sportsbet
vbet
vbet
mrbahis
mrbahis
hacklink
This post is on your page i will follow your new content.
AntwortenLöschenmrbahis
sportsbetgiris.net
sportsbet
mrbahis.co
sportsbet giriş
mrbahis giriş
casino siteleri
sportsbet
casino siteleri
Visit: rattan garden furniture
AntwortenLöschenThere are dildos, vibrators, simulated vaginas, blow-up dolls,ラブドール sex dolls full of holes, interesting hardware, all kinds of conquest gimmicks and other toys
AntwortenLöschenmecidiyeköy
AntwortenLöschensakarya
istanbul
kayseri
ordu
L7EYYB
artvin
AntwortenLöschenkastamonu
urfa
balıkesir
bitlis
K3VNN
whatsapp görüntülü show
AntwortenLöschenücretli.show
MMH
شركة تسليك مجاري بسيهات
AntwortenLöschenتسليك مجاري
https://istanbulolala.biz/
AntwortenLöschenET4ZA3
We are really grateful f평택출장샵or your blog post. You will find a lot of approaches after visiting your post. Great workk
AntwortenLöschenkayseri evden eve nakliyat
AntwortenLöschenaydın evden eve nakliyat
kütahya evden eve nakliyat
gümüşhane evden eve nakliyat
balıkesir evden eve nakliyat
TXBZ3X
düzce evden eve nakliyat
AntwortenLöschendenizli evden eve nakliyat
kırşehir evden eve nakliyat
çorum evden eve nakliyat
afyon evden eve nakliyat
QPİZU
24F1D
AntwortenLöschenKırşehir Şehirler Arası Nakliyat
Kütahya Lojistik
Kars Şehirler Arası Nakliyat
Bibox Güvenilir mi
Bolu Parça Eşya Taşıma
Muğla Parça Eşya Taşıma
Bingöl Lojistik
Etimesgut Parke Ustası
Burdur Şehir İçi Nakliyat
5585B
AntwortenLöschenAksaray Evden Eve Nakliyat
Çerkezköy Çekici
Referans Kimliği Nedir
Tekirdağ Parke Ustası
Bartın Evden Eve Nakliyat
Çerkezköy Korkuluk
Çerkezköy Motor Ustası
Bitlis Evden Eve Nakliyat
Çerkezköy Sineklik
4E4CC
AntwortenLöschenÇerkezköy Buzdolabı Tamircisi
Çerkezköy Yol Yardım
Erzurum Evden Eve Nakliyat
Bitfinex Güvenilir mi
Çerkezköy Sineklik
Kars Evden Eve Nakliyat
Yalova Evden Eve Nakliyat
Malatya Evden Eve Nakliyat
Eskişehir Evden Eve Nakliyat
EEB3E
AntwortenLöschenBinance Kimin
Bitcoin Mining Nasıl Yapılır
Bitcoin Madenciliği Nedir
Gate io Borsası Güvenilir mi
Binance Kimin
Binance Borsası Güvenilir mi
resimlimagnet
Ön Satış Coin Nasıl Alınır
Kripto Para Madenciliği Siteleri
8E50E
AntwortenLöschenBinance Neden Tercih Edilir
Madencilik Nedir
Binance Kimin
Yeni Çıkacak Coin Nasıl Alınır
Binance Neden Tercih Edilir
Kripto Para Nasıl Alınır
Bitcoin Nasıl Üretilir
Kripto Para Nasıl Oynanır
Kripto Para Oynama
888E6
AntwortenLöschenBitcoin Kazanma
Kripto Para Nasıl Kazılır
Coin Nasıl Çıkarılır
Coin Para Kazanma
Bitcoin Üretme Siteleri
Binance Neden Tercih Edilir
Bitcoin Nasıl Oynanır
Bitcoin Kazanma Siteleri
Kripto Para Nasıl Alınır
0757B
AntwortenLöschenBinance Kaldıraç Var mı
Bitcoin Çıkarma Siteleri
Yeni Çıkacak Coin Nasıl Alınır
Btcturk Borsası Güvenilir mi
Kripto Para Üretme Siteleri
Kripto Para Nedir
Binance Borsası Güvenilir mi
Bitcoin Kazanma
Bitcoin Yatırımı Nasıl Yapılır
F92ED
AntwortenLöschenresimlimagnet
7B8B7
AntwortenLöschenresimli magnet
resimli magnet
referans kimliği nedir
referans kimliği nedir
binance referans kodu
binance referans kodu
binance referans kodu
resimli magnet
binance referans kodu
9A0A2
AntwortenLöschenbitget
paribu
en düşük komisyonlu kripto borsası
bitexen
mexc
canlı sohbet ücretsiz
telegram kripto grupları
toptan sabun
en iyi kripto grupları telegram
E26F3
AntwortenLöschen4g mobil
telegram kripto
kucoin
canlı sohbet ucretsiz
en düşük komisyonlu kripto borsası
binance
binance
en güvenilir kripto borsası
kucoin
5F735
AntwortenLöschen----
----
----
----
----
----
matadorbet
----
----
gfhbgfhtfyjutfyu
AntwortenLöschenمهندس افران جدة
HJGKMH
AntwortenLöschenشركة تسليك مجاري بالدمام
hkjkghnhmhmhmj
AntwortenLöschenشركة صيانة افران
شركة مكافحة حشرات jKLjuxPHEi
AntwortenLöschenشركة مكافحة الفئران بالدمام CLGYL7AVFf
AntwortenLöschenThank you for your clear and engaging approach. It makes learning so much more enjoyable!
AntwortenLöschenKelly Reilly Floral Embroidered Denim Jacket
شركة تسليك مجاري بالاحساء rUtSMMeUSL
AntwortenLöschenشركة تنظيف بالقطيف YExENcK9g0
AntwortenLöschenشركة تسليك مجاري بالهفوف wx3XkfbIsz
AntwortenLöschen<a href="https://etaleya.com/%d8%b4%d8%b1%d9%83%d8%a9-%d9%85%d9%83%d8%a7%d9%81%d8%ad%d8%a9-%d8%
AntwortenLöschenwtf
AntwortenLöschenStand out like a champion in the England Lionesses purple puffer jacket, the ultimate blend of sporty elegance and bold fashion. Inspired by the fierce pride of England’s national women’s team, this eye-catching piece offers premium warmth and street-ready style. england merchandise football Whether you're a fan of women's soccer, a fashion-forward trendsetter, or simply love celebrity-inspired outerwear, this jacket delivers big on both comfort and statement-making flair. Perfect for winter fashion lovers across the USA who want to channel the power and pride of the Lionesses in every step.
AntwortenLöschenThanks for the great article.
AntwortenLöschenشركة تنظيف مكيفات بالبكيرية
At Starletcollections, apparel isn’t just fashion, it’s a statement. We started with a passion for timeless style and a belief that a outfit can be more than just outerwear. starlet collections Every piece we create blends craftsmanship, comfort, and bold design, tailored for men and women who dare to stand out. From classic cuts to modern trends, our leather jackets are made to last, empowering you with confidence every time you wear them.
AntwortenLöschen